Comparison With
Exposure Notifications System
In The United States

Governments and health authorities are working together to find solutions to the COVID‑19 pandemic, to protect people and get society back up and running.
Software developers are contributing by crafting technical tools to help combat the virus and save lives.
How Exposure Notifications Can Help
How Exposure Notifications Work
Download App
On Android, you can find the app for your area, if available, on Google Play.
If you have an iPhone, opt-in to Exposure Notifications in your device settings.

Generate Random ID
Once you opt-in to the notification system, the Exposure Notifications System will generate a random ID for your device.
To help ensure these random keys can’t be used to identify you or your location, they change every 10-20 minutes.

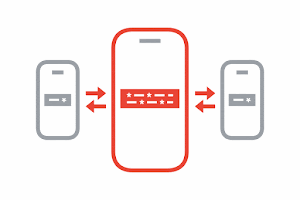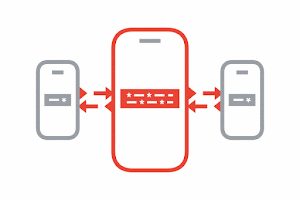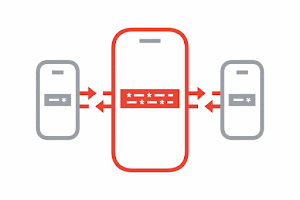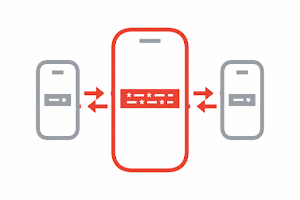
Exchange Keys through Bluetooth
Your phone and the phones around you will work in the background to exchange these privacy-preserving random keys via Bluetooth. You do not need to have the app open for this process to take place.
Check Keys Periodically
Your phone periodically checks all the random keys associated with positive COVID-19 cases against its own list
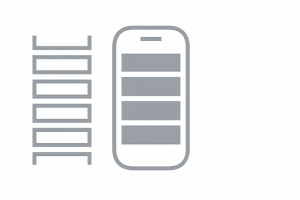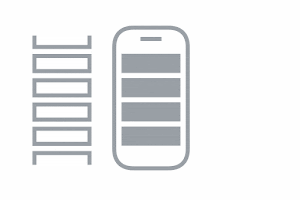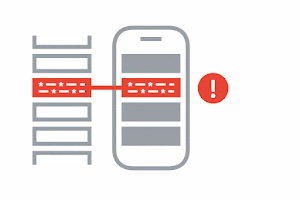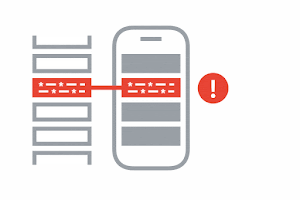
Exposure Notification
If there’s a match, you will receive a COVID-19 exposure notification, with further instructions from your public health authority on how to keep you and the people around you safe.

Exposure Notifications and Privacy

The Exposure Notifications can be turned off at any time.

The Exposure Notifications System does not collect or use the location.

The system does not share your identity with other users, Apple, or Google.

Only public health authorities will be able to use this system.
Exposure Notifications and Cybersecurity
National Institute of Standards and Technology (NIST) is building and demonstrating a secure, privacy-preserving, and robust implementation of exposure notification.
NIST’s cryptographic protocol distinguishes it from other exposure notification systems. The NIST approach does not record any information linked to individuals at any point throughout the entire process. It is impossible to rederive the identity of the devices, or of the device-owners, from the encounter IDs.


NIST’s approach to exposure notification, where z is the cryptographically secure encounter ID recorded by each device.
A different approach to exposure
notification, not developed by NIST.
The protocol permits third party correlation
attacks that could derive the identities.
Application in the United States
States with an exposure notification app on the National Key Server:
Comparison between China's Health Code and US's Exposure Notifications
Chinese Health Code
US Exposure Notifications
Health Code requires a mobile phone to generate a QR code.
Health Code collects the confirmed infection information, identity, certificate number for real name authentication, user-fill-in health information and other physical sign information.
Health Code uses GPS technology and collects user's location.
Health Code is almost mandatorily required in China if you want to enter public places or transportations.
Health Code is super widely adopted in China and have large amount of users.
Health Code is more efficient and accurate in detecting potential infected people.
Exposure Notifications have no "code".
Exposure Notifications collect only the "conversation" information of confirmed infected users' mobile phones in the whole process and do not collect user's identity information.
Exposure Notifications use bluetooth and do not collect location information.
Users has discretion as to the use of Exposure Notifications.
The application of Exposure Notifications in the United States is relatively limited.
Exposure Notifications do not have much effect due to insufficient number of users.


